UniSwap V2, Bot-LP frontrun. Full timeline breakdown ✅
We will be relaunching @ March 14th, 12pm ET
The Coinbase BTC ETF project, hits a small hurdle / a rock in the road / a malicious Uni V2 botter (exploiter), that’s been put down and put away.

- Bot, exploits and bonds our bonding contract.
- Instantly claims token the same minute.
- Approves UniSwap V2 pool for LP adding.
- Adds $BTC/ETH LP
- Withdraws majority sniper liquidity
Frontrunning $BTC claiming
A malicious UniSwap V2 bot, exploited our bonding contract on Base. And minted themselves $BTC tokens before the market and before open users.

In the above image, you can see the bot bond tokens.

This shows the bot, claiming 0.001 $BTC from the bond contract. That he initiated first. Instantly bonding & claiming to get $BTC tokens.
Adding $BTC/ETH LP to UniSwap V2

The bot then adds $0.04 of WETH LP, against $BTC. Deploying the UniSwap V2 pool. Snipers had pre-loaded our $BTC contract address into their tabs list, and loaded their wallets with ETH (Base) solely for our contract.
As soon as the LP was deployed, a majority batch of snipers, instantly bought the token.

Within the same minute, the bot then withdraw the LP for a $8,029 profit. They then tried to deploy SushiSwap pools, however the BaseBTCETF team blacklisted their LP pair before too many trades were initiated.
Several malicious sniper bots, then swapped into that LP pair. All aiming to front-run each other.

You can track the wallet who drained each other here:
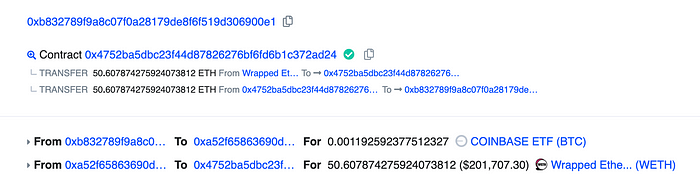
- Bought $0.45 — Sold $201.7k / https://basescan.org/address/0xb832789f9a8c07f0a28179de8f6f519d306900e1
- Bought $591 — Sold $96.6k / https://basescan.org/address/0xa76cc715f4366142ae5f036765de71eab933aec0
- Bought $197 — Sold $18.5k / https://basescan.org/address/0x00F4870732a65A3294687072aD2f335b76F6742A
For all users who may’ve bought into the early V2 contract.
